Hey folks, happy 2026!
As we start the new year, one thing every Windows admin should check off the list is verifying that your endpoints are ready for the Microsoft Secure Boot certificate transition. The old 2011 certificates start expiring in June 2026, and without the new Windows UEFI CA 2023 in place, devices won’t receive future boot manager security updates—leaving them vulnerable.
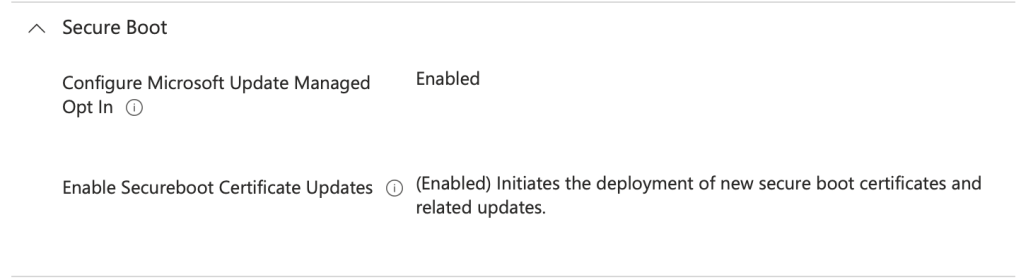
Microsoft is rolling out the 2023 certificates via Windows Update, but it’s smart to audit your fleet now and confirm the status. If you haven’t yet, make sure you have applied the needed Intune configuration profile your Windows endpoints through Intune:
Secure Boot CSP Documentation – Microsoft
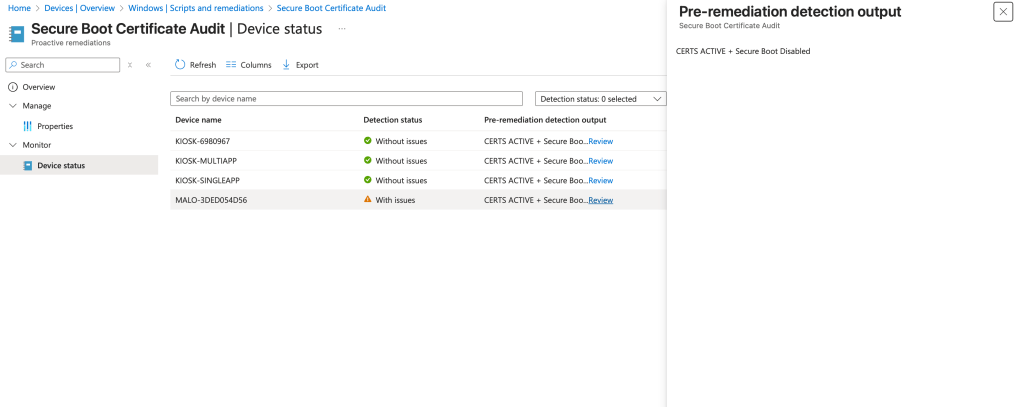
Next, you’re going want to audit your environment – so here is a script to help. Deploy this through Intune Detections & Remediations for a nice interactive report for review!
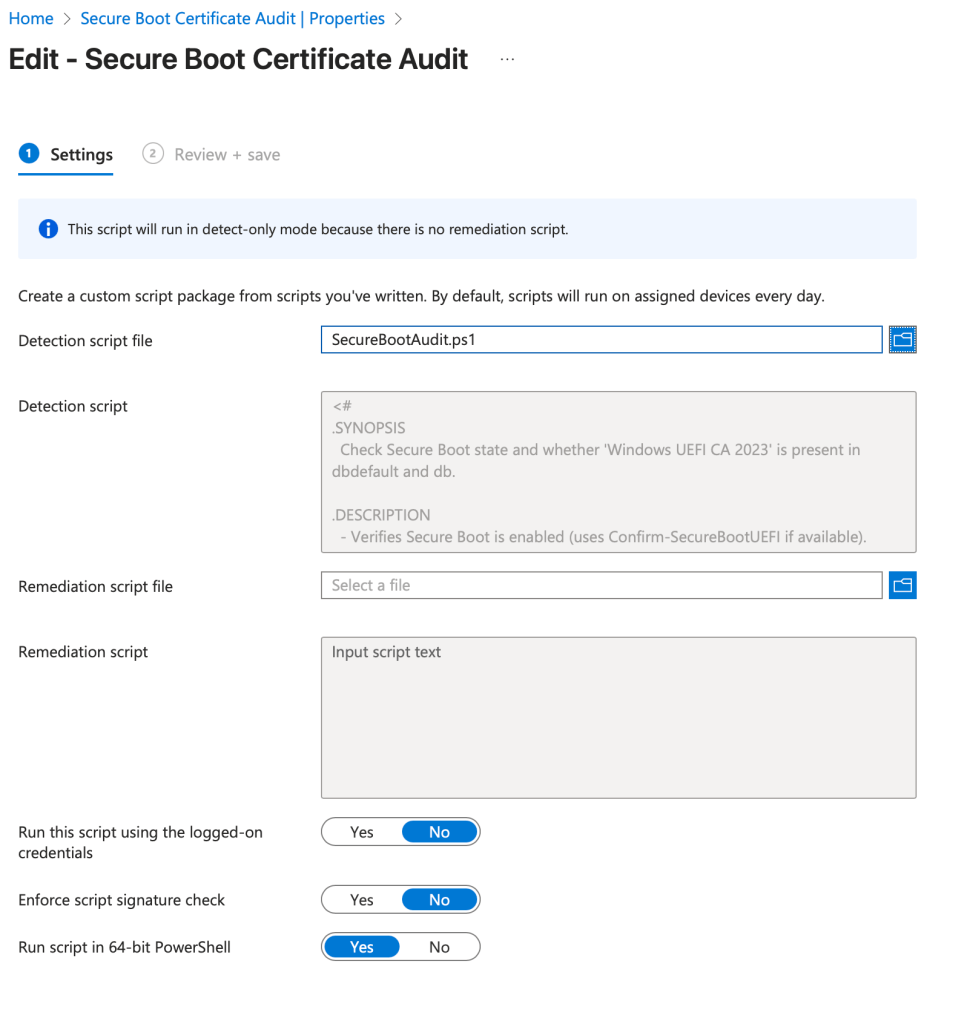
Here’s the script: GitHub Link
<#
.SYNOPSIS
Check Secure Boot state and whether 'Windows UEFI CA 2023' is present in dbdefault and db.
.DESCRIPTION
- Verifies Secure Boot is enabled (uses Confirm-SecureBootUEFI if available).
- Reads UEFI variables safely and searches for the certificate identifier.
- Outputs one of: SECUREBOOT_DISABLED, MISSING, ACTIVE, INACTIVE (and returns exit codes).
#>
[CmdletBinding()]
param(
[string] $ExpectedIdentifier = 'Windows UEFI CA 2023'
)
function Get-UEFIVariableBytes {
param([string] $VarName)
try {
$entry = Get-SecureBootUEFI -Name $VarName -ErrorAction Stop
if (-not $entry -or -not $entry.Bytes) { return $null }
return $entry.Bytes
} catch { return $null }
}
function Bytes-ContainsText {
param([byte[]] $Bytes, [string] $Text)
$encodings = @(
[System.Text.Encoding]::UTF8,
[System.Text.Encoding]::Unicode, # UTF-16 LE
[System.Text.Encoding]::BigEndianUnicode, # UTF-16 BE
[System.Text.Encoding]::ASCII
)
foreach ($enc in $encodings) {
try {
$decoded = $enc.GetString($Bytes)
if ($decoded -and ($decoded -match [regex]::Escape($Text))) { return $true }
} catch {}
}
return $false
}
# Secure Boot state
$SecureBootEnabled = $false
$SecureBootStateKnown = $false
if (Get-Command Confirm-SecureBootUEFI -ErrorAction SilentlyContinue) {
try {
$SecureBootEnabled = Confirm-SecureBootUEFI
$SecureBootStateKnown = $true
} catch {
$SecureBootStateKnown = $false
}
}
# UEFI db checks
$dbDefaultBytes = Get-UEFIVariableBytes 'dbdefault'
$dbBytes = Get-UEFIVariableBytes 'db'
$dbDefaultHasExpected = $dbDefaultBytes -and (Bytes-ContainsText $dbDefaultBytes $ExpectedIdentifier)
$dbHasExpected = $dbBytes -and (Bytes-ContainsText $dbBytes $ExpectedIdentifier)
# Cert status
if (-not $dbDefaultHasExpected) {
$certStatus = 'CERTS MISSING'
} elseif (-not $dbHasExpected) {
$certStatus = 'CERTS INACTIVE'
} else {
$certStatus = 'CERTS ACTIVE'
}
# Secure Boot wording
$sbStatus = if ($SecureBootStateKnown) {
if ($SecureBootEnabled) { 'Secure Boot Enabled' } else { 'Secure Boot Disabled' }
} else {
'Secure Boot Unknown'
}
# Compose single-line output
$line = "$certStatus + $sbStatus"
# Log: success only when Secure Boot Enabled AND Certs Active; else report issue
$success = ($certStatus -eq 'CERTS ACTIVE' -and $SecureBootEnabled -eq $true)
if ($success) {
Write-Output $line
exit 0
} else {
Write-Output $line
exit 1
}
Apply this script through Intune Detections and Remediations for a nice visual report regarding Secure Boot! Here are the setting you need to get this rolling in Intune!

Leave a comment